OpenWRT is an open source firmware for routers and AP’s that unlocks many features not usually available. This firmware will allow us to use the radio’s on the AP’s as mesh-point interfaces and also we can bridge the interfaces to the Ethernet ports so the devices act like one giant switch.
Loading OpenWRT On To The AP
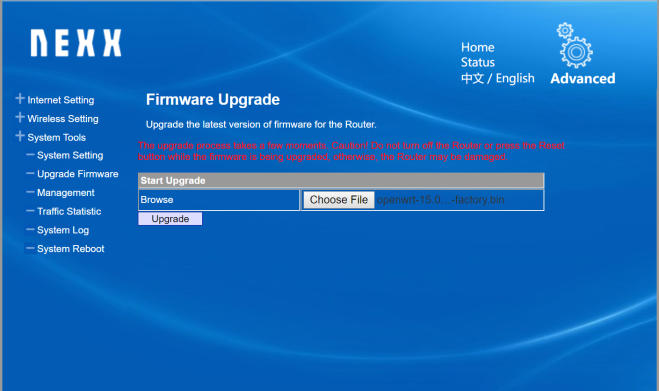
When we first log in to the AP we are greeted with the NEXX configuration portal login screen. We simply navigate to the firmware upgrade page and point to the: openwrt-18.06.1-ramips-mt7620-wt3020-8M-squashfs-sysupgrade.bin file I downloaded earlier. The whole process took about 5 minutes.
When we next try to login to the router, success is confirmed by the OpenWRT configuration login screen.
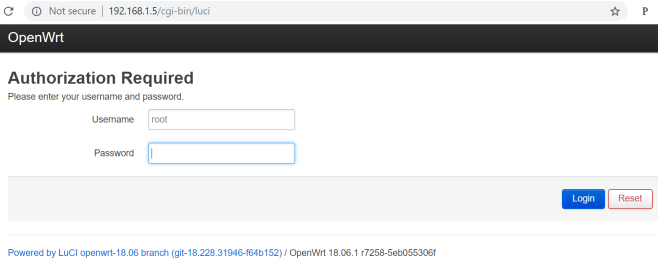
After changing the root password, SSH access to the AP becomes possible for more advanced configuration.
Configuring The AP for 802.11 Mesh
Once we have the firmware installed on the devices, the configuration is relatively straightforward. We edit /etc/config/wireless
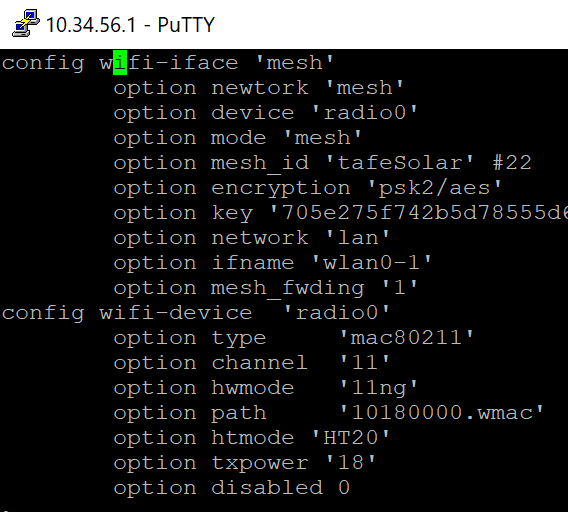
What this does is create a 802.11s mesh interface called “mesh” and it is linked to the “lan” interface, which means the mesh will create a single logical layer 2 domain.
Also the radio0 interface was switched on as it’s disabled by default. Finally the AP configuration section was completely removed as we’re not using these devices for Wi-Fi at all. This will improve security as the device will not be visible to anybody unless they are running specific software. It will also improve performance because the device will not be using the single radio for both AP mode and 802.11s.
Next we edit /etc/config/network to assign ip addresses to the LAN ports and set them to bridged mode, effectively making it so that any device connected to an AP in this mesh network will be connected as if they were all plugged in to the same switch. This will allow us to feed all the data we collect to the raspberry pi easily and with no need for major cabling.
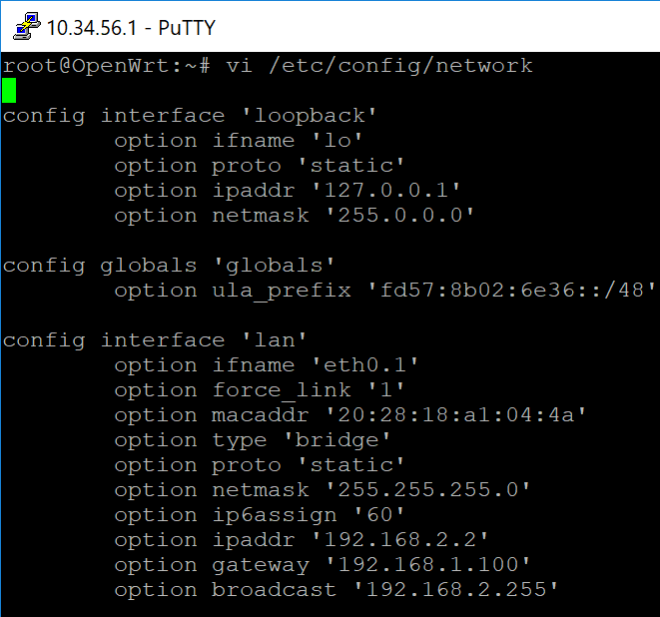
The beauty of this configuration is that it’s completely modular, if we want to add a new device to the network we simply load this configuration onto a new AP and it will add that device to the layer 2 topology.
Verifying Connectivity
Once we have set the configuration we can reset the services with the “wifi” command. We can verify the ap mesh interface is running with “iw dev wlan0 station dump.”
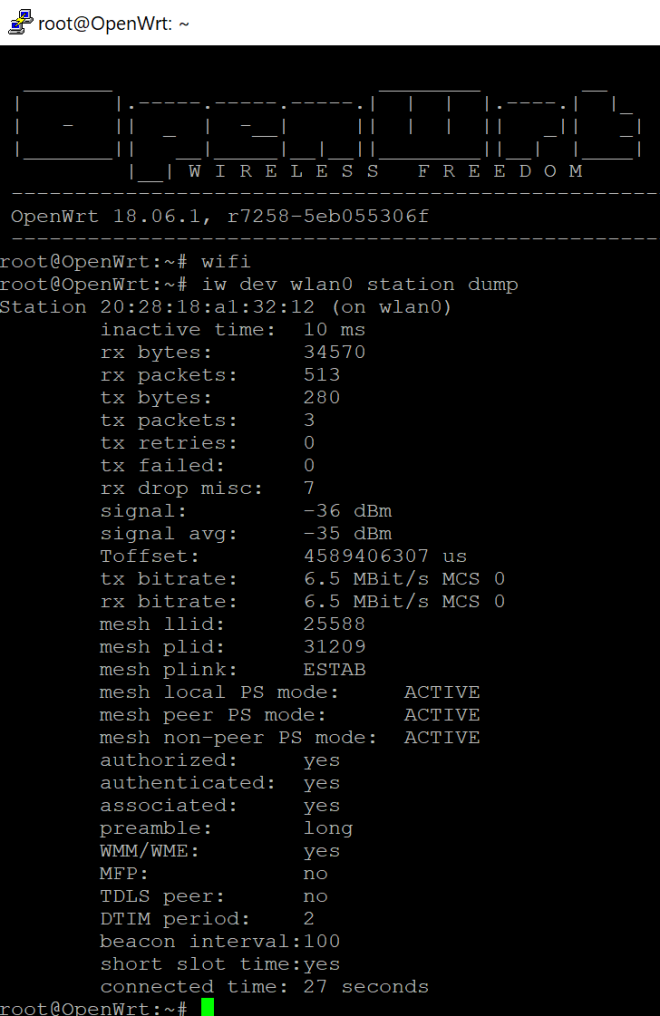
The output confirms that the mesh node is active. To check the status of peers we run “iw dev wlan0 mpath dump”.
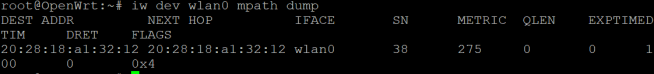
This shows the mesh link to the other node is active. Basic connectivity is confirmed by pinging from one AP to the other.
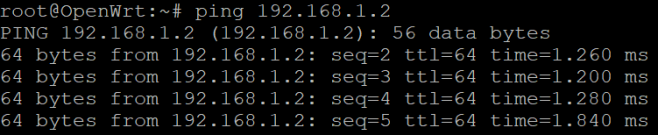
Using the Nexx AP’s with this configuration, we can add an arbitrary number of devices to the network quickly, cheaply and securely. The next step is to install the AP’s at Ultimo and start sending data to the raspberry pi.

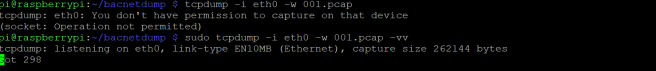
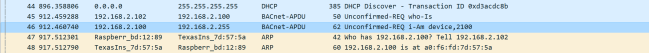
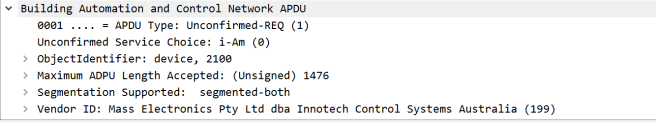
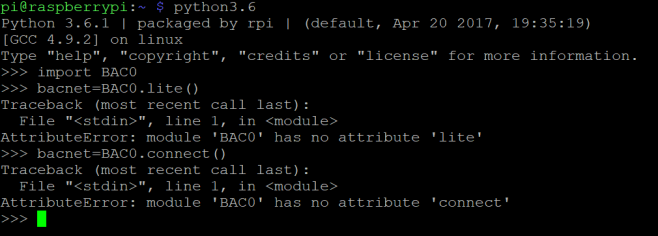
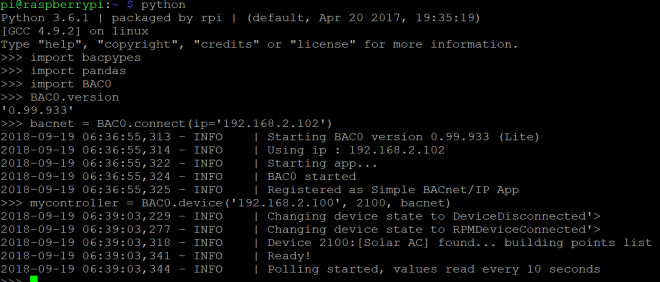
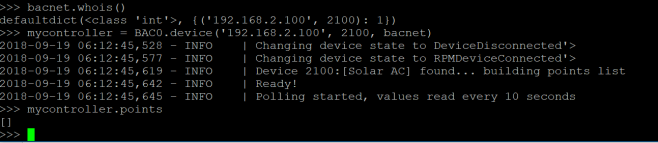
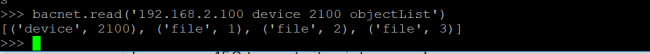
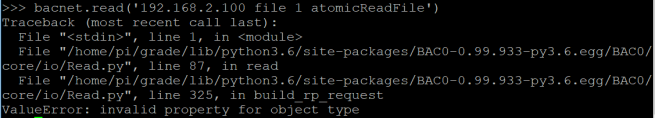
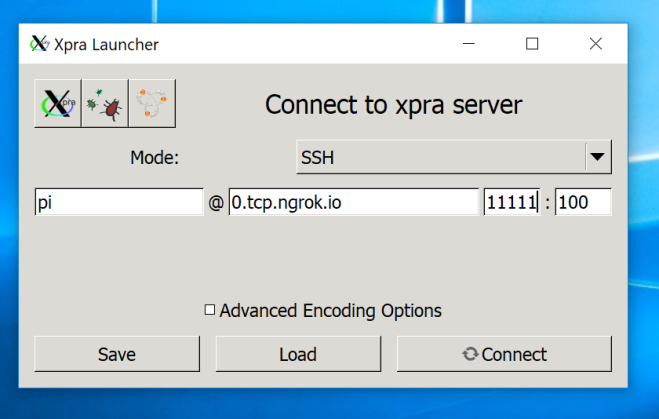
 The above command launches an xpra output of the midori browser, that I can connect to on my windows machine. The process can be repeated to launch any program that requires graphical output. The screen program allows the daemon to run in the background after I disconnect.
The above command launches an xpra output of the midori browser, that I can connect to on my windows machine. The process can be repeated to launch any program that requires graphical output. The screen program allows the daemon to run in the background after I disconnect.